A thriving black market for stolen identity data has sprung up on the dark side of the World Wide Web. Various attack techniques are used to obtain the requested information. A strategy that is often used and promising at the same time is the man-in-the-middle attack. In the following sections we will tell you exactly what is hidden here and how you can protect yourself and your company from them.
Digital identity data is the focus of desire for cybercriminals – be it to sell it on the illegal black markets on the dark web, or with the aim of using it for sole fraudulent finesse. It is no coincidence, then, that more and more threat actors are chasing them at tremendous expense – and in some circumstances even at great expense.
Just in the last few years, for example, in the course of a series of large-scale Internet attacks on well-known companies, several million pieces of identity data have been stolen and disclosed.
In order to obtain the requested data, threat actors resort to the repertoire of modern, but also older, attack methods such as man-in-the-middle, also known as Janus attack and middleman attack.
How do man-in-the-middle attacks work?
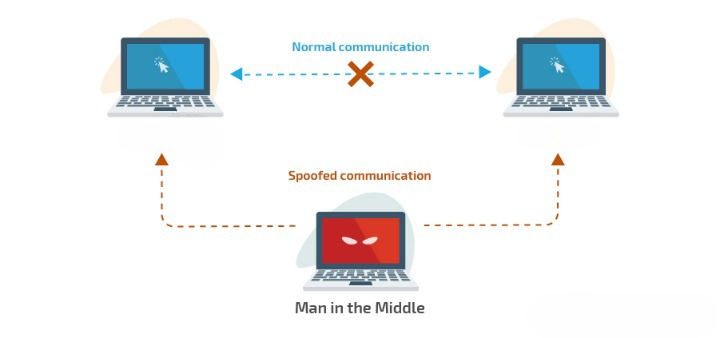
Man-in-the-middle is an attack strategy in which the threat actor secretly infiltrates the data communication of two or more communication partners. In doing so, he puts himself in a position where all traffic is navigated through his private systems, putting him in a position to stop, eavesdrop, or even just tamper with valuable identity data.
For a man-in-the-middle attack to work, it is important that the same threat actor remains undetected. To do this, it first places itself or malicious software between the victim and the Internet resource used by the victim, such as an email account. This then poses to the victim or resource as the actual communication participant.
With placement, the threat actor is able to inspect all data communications between the victim and the Internet resource, as well as tamper with it for its own benefit in order to initiate further prohibited operations, such as forging transactions or stealing intellectual property.
The Different Types of Man-in-the-Middle Attacks!
Over the years, threat actors have created various opportunities for man-in-the-middle attacks. Depending on the application, different attack variants and attack methods are used. The most used are:
Evil hotspot/ rogue access point:
With this attack technique, threat actors set up their WLAN access point, i.e. hotspot, in a public WLAN network in order to trick nearby end devices into joining their domain. If an employee connects to the supposedly open WLAN, those threat actors would be able to examine and manipulate all data communications.
In the attack vector, the threat actors exploit a vulnerability in the “real” router to “eavesdrop” on data communications between that router and a user. In contrast to the evil hotspot, this procedure promises a greater profit, since a significantly larger amount of valuable identity data can be read out over a longer period of time.
Man-in-the-browser attack:
With this attack technique, malware is installed in the browser of the internet user or employee. The attack method works best as soon as the software used on the affected computer is not up to date and therefore shows security gaps. In addition, browser plug-ins are used in this form of attack because they store the data communication from the infiltrated user and the websites visited.
DHCP-based attacks/DHCP spoofing:
In DHCP-based attacks, threat actors pose as DHCP servers on a LAN. In this way, they can regulate the assignment of IP addresses, enter different standard gateways and DNS servers and in this way redirect data communication to their systems in order to intercept or manipulate them. This is also called DHCP spoofing. The key to the attack’s triumph is that the threat actor be on the same LAN as its target.
ARP Cache Poisoning:
In this version of the attack, threat actors start by mapping a MAC address to the local IP. To do this, they fake the ARP tables to present the computer as a WLAN access point. Once ARP spoofed, threat actors can read or record all outbound traffic before it is sent to the real gateway. Here, too, it is essential for the success of the attack that the threat actor and the victim are on the same network.
DNS-based attacks:
With the DNS-based man-in-the-middle attack, the entries in the cache of a DNS server are falsified. The goal here is for the DNS server to respond with incorrect, defined target addresses. In this way, a victim can be directed unnoticed to any website that may have been manipulated. Such an attack is successful by abusing security gaps in older DNS servers.
How can you protect yourself against man-in-the-middle attacks?
First of all: Without the appropriate measures, it should be difficult to detect man-in-the-middle attacks. In many situations, data communication is not even read for a long time, as long as there is no obvious manipulation of very present message content. For this reason, man-in-the-middle attacks are only noticed when it is already too late.
Since man-in-the-middle attacks can cause considerable damage, they should ideally be prevented or warded off from the outset. A reliable protection mechanism can only be achieved here by combining various IT protection measures.
These include, among other things:
• secure WEP/WPA encryption on these access points
• secure encryption and login information on your routers
• use of virtual private networks
• use of HTTPS as a communication protocol or encryption with SSL / TLS
• authentication based on various aspects
• use of strong passwords
• Avoid using insecure LAN and WLAN connections
• Always keep systems, tools, software and browsers up to date
• Knowingly remove security gaps
• Respect common measures against phishing
Also Read : 5G Technology, Main Sectors That Will Benefit From Its Speed